Creating a Full File System image from a jailbroken iOS device
In this post Nick Dubois introduces a variety of concepts to prepare you for creating a forensic image from a device that has been jailbroken with unc0ver. He demonstrates how to do this 9 different ways including freeware and multiple manual methods. The appendices that follow assess the testing that was done with each of these methods.
Foreword
This blogpost outlines nine different ways to create device backups (Both Logical and Full Filesystem). See our related “Jailbreaking iPhone XR with unc0ver” blogpost to learn more about jailbreaking iDevices with Unc0ver.
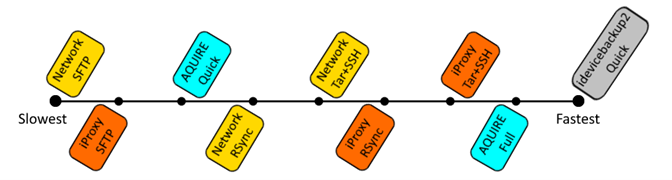
Speed Comparsion of different iOS image methodologies
Risks
Jailbreaking comes with risk. To mitigate these risks, attempt to jailbreak a test device of the same model and same iOS version. Determine if the jailbreak in question functions better when settings are changed; some exploits provide a much lower failure rate when airplane mode is turned on and other features are turned off. Turning off certain settings should be standard practice to avoiding remote device reset.
Safemode
Safe Mode
Certain jailbreaks, when failed, will enter a device mode known as “Safe Mode”. In this mode the device is successfully jailbroken yet a service or "tweak" has caused an error. Safe Mode is not a full device reboot; clicking on the “Restart” button should fix the jailbreak.
Rebooting
An unsuccessful jailbreak will oftentimes reboot the device. Once rebooted, a password must be entered (or bypassed) before another jailbreak may be attempted. Ensure a password has been recovered before attempting a jailbreak with a high failure rate. This does not apply to certain BootROM/startup jailbreaks such as Checkm8.
Boot Loops
If a device is pushed into a boot loop the examiner may be able to force restart it using the home button + power button or power button + volume button. Note that restarting a device will disable faceID or touchID features until a password is entered. (May also limit USB functionalities) Some boot loops are not escapable using buttons, the examiner may try to enter DFU mode or some other mode through USB, if this does not work the examiner must unplug the device and wait until it dies.
Device Brick
In a worst-case scenario, a jailbreaking attempt may brick a device. A bricked device may boot loop forever even once force reset or simply present a black screen. A bricked device may be recovered through exploits which attack the bootloader directly, however generally fixing a bricked device means factory resetting it. (Complete loss of evidence) To best mitigate risks jailbreak a test device first (several times), charge a device enough so that it will not die during the jailbreak process, and do not jailbreak the device immediately after boot (Give it a few minutes to startup).
See Appendix I. which details the success and reboot rate of certain jailbreaking applications
Creating an FFS
The process of creating an FFS is seemingly straightforward – obtain root device permissions, navigate to the root directory of the filesystem, copy over every file on the device recursively while causing minimal modification. Doing this however is easier said than done. Several software may assist us during the FFS recovery process.
Before determining which recovery method to use, examine Appendix II. “Efficacy of Image Recovery Methods”.
FFS Via Magnet AQUIRE
Magnet AQUIRE is a free forensic acquisition tool offered by Magnet Forensics. AQUIRE has several benefits; it is well-developed and reliable, it supports logical and FFS recovery, it supports many devices, it creates image hashes and useful diagnostics automatically, and it offers a straightforward Graphical User Interface (GUI).
To install Magnet AQUIRE navigate to the following link and fill out the request form for the free tool: https://www.magnetforensics.com/resources/magnet-acquire/
iTunes - but not via the Microsoft store
iTunes
Before starting Magnet AQUIRE ensure the latest version of iTunes is installed. iTunes contains drivers and services required for comprehensive communication between iOS devices and PCs. Ensure the application is installed natively (not through the Microsoft store). To install iTunes, head over to the following link: https://www.apple.com/itunes/, navigate to “Looking for other versions”, and download the iTunes setup for Windows or macOS respectively.
1. Logical (Quick) Image
A Logical, or “Quick” image can still provide plenty of data. When a device is not jailbroken (and computer trust is established – passcode is required for newer models) a logical image may be gathered. To create a logical image connect the iDevice into the PC, select the device once it appears in AQUIRE, and follow the image creation wizard.
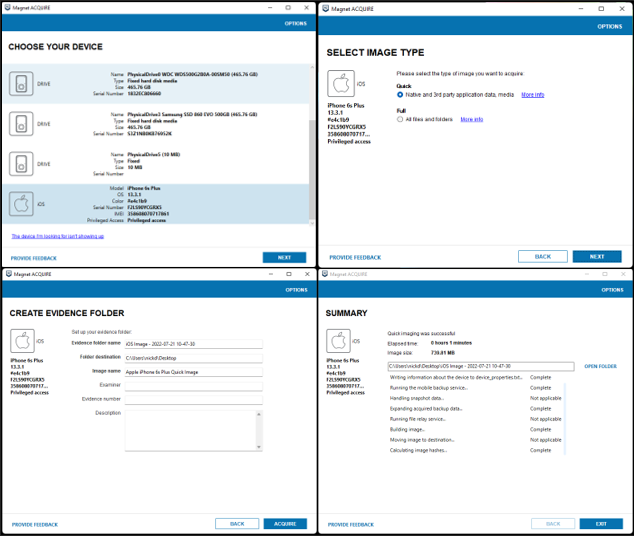
Using Magnet ACQUIRE to create a Full File System (FFS) Image
2. Full File System (FFS) Image
Obtaining an FFS with Magnet AQUIRE is as straightforward as obtaining a Logical image. Navigate through the menu as per usual and select “Full” in the image type menu. This option is only available when the connected device is jailbroken, and root access is visible. Note that occasionally AQUIRE may not provide this option even when the device is jailbroken. This is an uncommon bug and restarting the application should fix it.
Using Magnet ACQUIRE to create a Full File System (FFS) Image
Shortcomings
As convenient as the software is, Magnet AQUIRE is not absolutely perfect and on occasion an iOS device (or iTunes drivers) may not play nicely with the software. USB Connection is required throughout the recovery process. If facing issues with USB or a device is not showing up in the device selection menu, consider using another USB cable. If swapping USB cables does not remedy the issue, the following recommendations may help:
Restart Magnet AQUIRE a number of times
Manually restart Apple Services
Reinstall iTunes
Restart PC
Re-Jailbreak the Device
SSH Setup
The following three recovery methods will utilize the Secure Shell (SSH) protocol. SSH must be installed and configured on the iOS device while, or after jailbreaking.
SSH Setup (Unc0ver)
SSH Setup
If a device is compatible with the Unc0ver jailbreak, the examiner may install SSH directly through Unc0ver. Doing so directly through Unc0ver means the examiner does not have to install the package management application (Cydia) and may make as few modifications to the filesystem as possible.
To install SSH first open the Unc0ver application, navigate to the settings icon, enable the “(Re) Install OpenSSH” option, disable all other options, and proceed to jailbreak the device.
You may now SSH into the device manually using putty or cmd prompt. Username:root Password:alpine
SSH Setup (Checkra1n)
Simply jailbreak the device. SSH is automatically installed, there is no need to install Cydia.
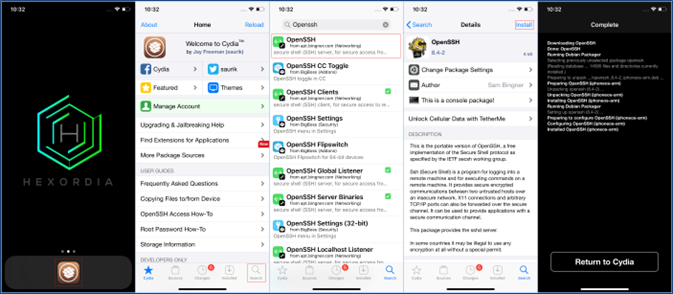
SSH Setup (Cydia)
Other jailbreaking applications may or may not offer similar settings to enable SSH during installation, always test with a test device before attempting to jailbreak and setup SSH on an important device. When no SSH installation option is available for the iOS version the examiner is working with, they may instead install the Cydia application.
Once Cydia is installed on a device, SSH may be installed by navigating to the search menu, typing in “OpenSSH”, and proceeding to install. You may now SSH into the device manually using putty or cmd prompt. Username:root Password:alpine
FFS Via libimobiledevice
Libimobiledevice is a library consisting of several programs created to interact with iOS devices over USB connection. Libimobiledevice is well documented at: https://libimobiledevice.org/. The software may be installed and compiled manually, see the website for more details. The software is compatible with Linux, Windows, and macOS.
Source code may be found at https://github.com/libimobiledevice/libimobiledevice
Pre-compiled copies of libimobiledevice may be found at the following link: https://github.com/iFred09/libimobiledevice-windows
3. idevicebackup Logical Image
A logical image/backup may be created using the idevicebackup or idevicebackup2 tools included in libimobiledevice. To create a Logical backup using libimobiledevice, use the command: [Path to idevicebackup2.exe] backup -- full [Output Directory] Note that for devices running iOS 3 and below, use idevicebackup.exe
USB Restricted Mode
To create an FFS Image first disable USB Restricted Mode (USBRM) manually. To do so ensure the device is unlocked and enter the followin command: [Path to idevicepair.exe] pair Once entered, a “Trust” prompt should appear on the device. Click on “Trust”.
iProxy Setup
An FFS image may be recovered from jailbroken iOS devices with SSH installed. The iproxy tool included within libimobiledevice is used to setup a speedy SSH connection over USB. To use iProxy enter the following command in a designated command prompt: [path to iproxy.exe] [Local SSH port] [iOS SSH port]
The Local SSH Port may be set to any port which is not used by another service on the host machine. I will use 1111 for example. The iOS SSH Port should be set to the port running SSH on the iOS device (22 for Unc0ver and manual, 44 for Checkra1n). Note that when SSH is installed manually (OpenSSH), SSH port should be set to 22. When jailbreaking with Checkra1n however SSH is setup on port 44.
Example of running iproxy on port 22
4. SFTP Connection and Recovery
Secure File Transfer Protocol (SFTP) establishes a connection between devices over the Secure Shell (SSH) protocol. Once established, the SFTP connection allows devices to push and pull files to and from each device.
To connect to the device, open another command prompt and type the following command: sftp -P [Local SSH Port] root@localhost
Once prompted, enter the password “alpine”. After a connection is established, recover the filesystem with the following command: get -arp ../../../ [Output Directory]
Example of using SFTP Connection
When connecting to multiple devices, the RSA key may change and trick your PC into thinking it is under attack. The PC will no longer allow an SSH or SFTP connection when this happens. If an error occurs, try removing the file located at: C:/Users/[user]/.ssh/known_hosts.
5. RSync Connection and Recovery
RSync is another protocol for remote file transfer; similar to SFTP. RSync is noticeably faster and provides more functionality. Before using RSync, it must be installed on the iDevice. Intstall the “rsync” package through Cydia, or SSH into the device and install RSync using the following command: sudo apt install rsync
RSync must then be installed on the host PC. RSync may be installed on Mac/Linux machines using apt and homebrew, yet RSync does not natively support Windows. In order to use RSync with Windows an examiner may use the package “cwRsync”. cwRsync is an RSync client created specifically for Windows. Visit the following link to install cwRsync: https://www.itefix.net/cwrsync
Navigate to “Free Rsync Client” and install the appropriate zip file for your Windows installation. SHA hashes are provided on the website. Once downloaded, unzip the archive. Take note of the following files in the directory: cwrsync/bin/rsync.exe and cwrsync/bin/ssh.exe. These two files will provide the RSync functionality we need on Windows.
cwRsync is not configured to work well with ports other than port 22, so when configuring iProxy use port 22 for the Local SSH Port. E.G.,
Configuring iproxy to use port 22
Once iProxy is configured, cwRync may be used to recover the FFS. I have opted to use the following command to recover an FFS: [Path to rsync.exe] -e [Path to ssh.exe] --port=22 -r -P -W -D -S --no-compress --links --hard-links --executability --devices --specials --xattrs --owner --group root@localhost: ../../../* [Local Output Path] The path must be local (not global) as cwRsync considers any path with a colon “:” as a remote path. RSync is extremely malleable and offers many options to tweak. To see other options, go to the following site: https://linux.die.net/man/1/rsync
6. Tar + SSH Connection and Recovery
There are benefits of using the Tar + SSH file transfer method; the image is placed into a single tar file, (not compressed although this is an option “-z”) only SSH needs to be installed, and the recovery time is much faster than most other methods discussed. Tar offers many options see the tar man page: https://man7.org/linux/man-pages/man1/tar.1.html To initialize recovery using tar and ssh, use the following command: ssh root@localhost tar cfp - / > [output file].tar
Note: The message “Exiting with failure status due to previous errors” may appear. A few files have likely not been copied over due to permission confliction, yet the entire filesystem should be in the tar without issues.
7. FFS Via Network SFTP
Although using libimobiledevice will provide the best (fastest) experience, examiners need to have a backup prepared in the case a mobile device or host computer does not play nicely with the library. An SFTP connection may be made over a local network rather than through USB. A wireless network connection is exponentially slower than a wired connection, however direct SFTP is a great backup option. Do not connect to a Wi-Fi network unless you are certain that the device is not going to reset! Connect to an internal network which is not connected to the internet.
Find the local IP Address of your iDevice. Go to Settings à Wi-Fi à Click the “I” next to the attached network. Note the “IP Address” section. You may now manually SSH into the device using putty or cmd prompt. Username:root Password:alpine
Finding the local IP address
Rather than SSHing into the machine, connect to it with SFTP using the following command: sftp root@[IP Address] Once connected, recover an FFS image using the following command: get -arp ../../../ [Output Directory]
8. FFS Via Network RSync
RSync may be used over the network similarly to SFTP. An examiner will need to install rsync through the Cydia application (or through apt after sshing into the device). Once RSync is installed, they may use it to recover the Full FileSystem much faster than FFS recovery with SFTP.
Interestingly, the “raw” speed of the RSync transfer is not much faster as that of the SFTP transfer, however the rate at which RSync is able to identify and switch which file is being transferred makes the protocol exponentially faster. Examine Appendix II. and note how the rate at which the iPhone 6s+ recovers data with RSync is much faster than SFTP, yet the rate at which the iPhone X recovers data with RSync is not as much faster than SFTP. This is because the bulk of data on the iPhone X are large videos and images. Speed is saved with smaller and constant file transfers while less time is saved with large file transfers.
Older devices may not support the SSH algorithm used by default. The option may be changed with the ‘-oHostKeyAlgorithms=+ssh-dss’ flag as depicted below:
9. FFS Via Network Tar + SSH
Tar + SSH may be used to acquire an FFS imagfe over a network. The same command is executed as with iProxy Tar + SSH, yet in this case we will point to the remote IP address rather than ‘localhost’: ssh root@[IP Address] tar cfp - / > [Outfile].tar
Appendix I.
Efficacy of iOS Jailbreak Software
For n=50 trial jailbreak attempts per device
Efficacy of iOS Jailbreak Software
Appendix II.
Efficacy of Image Recovery Methods
Note: Time may vary due to network speed, device model, recovery protocol. Individual file size, local computer processing power, USB speed/generation, and hard drive speed.