What's brewing with IPAs - Working with IPA files for Forensic Examiners
iOS App Store Package (IPA) files are to the iOS operating system what Android Package (APK) files are to Android operating systems. The IPA filetype is nothing more than an archive and may be explored with any file explorer. (The same is true with APK files)
To open up an IPA (or APK) file, simply use a robust file explorer such as WinRAR or 7-Zip. Alternatively, rename the IPA file to the “.zip” extension. The file may now be extracted and handled as any ordinary ZIP.
Renaming the IPA as a .zip file
IPA File Structure
The extracted IPA will contain a folder titled “Payload”. The Payload directory will contain the applications “.app” folder. The app folder contains the default application. The IPA will likely (though not technically mandatory) contain an “iTunesArtwork” file along with an “iTunesMetadata.plist” file.
File structure of Snapchat.ipa folder
iTunes Artwork
The “iTunesArtwork” file is a simple PNG or JFIF/JPEG file (may vary). To view the image, rename the file to the “.png”, “.jfif”, or “.jpg” extensions as appropriate.
Renaming iTunesArtwork as iTunesArtwork.png
iTunes Metadata PList
The iTunes Metadata file will contain information such as the iTunes user who had purchased the application, purchase timestamp, and application information. Note that applications installed from an unofficial app store or through a manual IPA install will not necessarily present the Apple ID of the device owner but may present the Apple ID of whichever user originally made a copy of the application.
List view of the iTunesMetadata.plist
IPA Installation
IPA files may be installed onto a device manually. Manual IPA installation provides a way to test applications in development and/or install unofficial applications.
Backend Operation
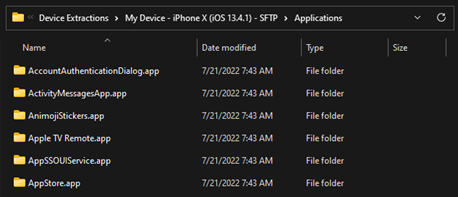
As an IPA is installed, several actions take place in the background of the device. Understanding these actions may help understand how to analyze the applications later on. As the user installs the application, contents of the “.app” folder are extracted and copied to their respective locations on the device. For system applications (and jailbroken applications) this will be contained within the “/Applications” directory on the device.
Contents of the /Applications directory
For standard (non-system) applications, app folder contents will be extracted to the “/private/var/containers/Bundle/Application/[AppGUID]” directory. Notice how the íTunesMetadata.plist” file is also copied over to the directory.
Contents of the /Bundle/Application/[AppGUID] directory
Populated application data will not modify the original IPA nor the application bundle. When installing an application from the app store, the IPA only exists temporarily until extraction and installation are finished, at which point the file is disposed of. Once installed, a Data folder is created for the application data. This directory may be found at “/private/var/containers/Data/System/[AppGUID]” for system applications and “private/var/mobile/Containers/Data/Application/[AppGUID]” for non-system applications.
Contents fo the /Data/Application/[AppGUID] directory
Note that examiners cannot see the application directories unless they have the capabilities to jailbreak the device or obtain a full filesystem recovery.
IPA Files in Relation to Jailbreaking
Applications used to jailbreak iDevices must be installed through the sideloading of IPA files. Such applications (e.g., Unc0ver, Yalu, Pangu, Houdini, etc…) are not available on the Apple App Store as they take advantage of device exploits to provide a higher level of access. Several IPA installation techniques are discussed in greater detail below.
I have forgone the inclusion of the official XCode application for macOS in this blog post. To see how to upload an IPA file with XCode, head over to our blog post on “Jailbreaking an iPhone XR with unc0ver”.
IPA Installation Via Sideloadly
Sideloadly is a desktop application for sideloading IPA applications onto jailbroken and non-jailbroken iDevices. Sideloadly is well-maintained and frequently updated. Follow the installation instructions detailed on the official website, take special care to ensure that the web version of iTunes is installed or else the application will not function as intended. Cydia Impactor is a similar tool, yet Cydia Impactor has not been maintained for some time and no longer works unless the user has a paid Apple developer account.
Install Cydia Impactor here: http://www.cydiaimpactor.com/
Install Sideloadly here: https://sideloadly.io/
Once Sideloadly has been installed, execute the program, connect your target iDevice, select an IPA and Apple ID, and start uploading.
Using Sideloadly to upload an IPA
Once the application has been uploaded It should appear on the devices’ home screen. Clicking on the application will present the “Untrusted Developer” message.
To fix this problem head to settings 🡪 General 🡪 Device Management and trust the application. The application may now be opened from the home screen. When the profile expires, this application is no longer able to be opened. With Sideloadly, the profile will have a 7-day expiry period.
Establishing trust for the sideloaded application
Here is a video of using Sideloadly! to sideload an iPA.
IPA Installation Via AltStore
AltStore will sideload IPA files from a PC onto an iDevice. This program offers several options in terms of extending application certificates, however from my experience this program is not as stable as Sideloadly when it comes to flashing the applications.
Visit the following link to install AltStore: https://altstore.io/
To install the AltStore application onto the iDevice, run the installed “AltServer” program on a host PC (may have to run as Administrator). Head to the tray to the right of the Windows taskbar, click on the AltStore icon, and Install AltStore onto the device.
Installing the AltStore application on the iDevice
Once installed, open the AltStore app and click on the “+” to install an IPA. In this case the IPA must be downloaded onto the iDevice locally. When installing an application, the device must be connected to the AltServer instance.
Installing an IPA with AltStore
AltStore provides the benefit of refreshing certificates. To refresh a certificate, connect the device to a PC with AltServer active and click on the “Refresh All” option.
IPA Installation Via OTA
Over the Air (OTA) application deployment allows users to install applications over an HTTPS connection (no computer required). There are two methods for installing applications over OTA.
Third-Party Source / Third-Party App Stores
Applications may be installed from a third-party source. These sources host the IPA file online for mass consumption. Security should be taken into consideration as many sources upload malicious renditions of applications in order to steal information from unknowing users. The third party may accept application submissions from external sources and are now unknowingly hosting malicious applications. With this risk in mind, the following websites provide OTA application deployment:
Personally, I do not recommend using these websites as manual installation is much safer. There is no knowing when the application certificate will get revoked by Apple and finding a working certificate is often more hassle than generating one manually.
Manual OTA Deployment
Manual OTA deployment allows users to upload an application to an online service and then install it on an iDevice. The user should take security into account here as well. For the most part OTA application deployment is safe when the user can ensure the IPA file they upload is safe, however the application uploaded may be modified or swapped with another application prior to download (as you are uploading to a server not under your control). If the application contains sensitive information, it should absolutely not be uploaded to such a website as we do not know who can examine the upload. The following websites provide manual OTA deployment services:
https://developer.apple.com/testflight/ (Official for Apple Developers)
https://appdb.to/ (Paid Edition Only)
https://appho.st/ (Free / Paid)
https://www.installonair.com/ (Free / Paid)
https://www.diawi.com/ (Free / Paid)
IPA Extraction / Backup
Extracting an IPA file directly off of an iDevice is useful for several reasons:
The IPA may preserve the application version
The IPA may be installed on other devices
The IPA may be modified, or reverse engineered
Extracting an IPA file is only possible when the user has access to the “Bundles” directory. This is because the IPA must be repackaged as the original one was deleted after extraction and installation (if installed via the app store). Interestingly, this does mean that even System applications may be packaged into IPA files.
IPA Extraction Via FFS
It is easy to obtain an IPA file of an application if the examiner has already acquired a full filesystem image of a device. First open the target FFS extraction and head to the application bundle which you wish to backup. The bundle will be contained at “/private/var/containers/Bundle/Application/[BundleGUID]”. To correlate Bundle GUIDs with their associated applications I suggest examining the following files:
/private/var/installd/Library/Logs/MobileInstallation/mobile_installation.log.0
/private/var/mobile/Library/FrontBoard/applicationState.db
Note: To find all applications I suggest examining the following files:
/private/var/installd/Library/Logs/MobileInstallation/mobile_installation.log.0
/private/var/mobile/Library/Application Support/com.apple.remotemanagementd/RMAdminStore-Local.sqlite
/private/var/mobile/Library/FrontBoard/applicationState.db
/private/var/db/lsd/com.apple.lsdidentifiers.plist
/private/var/containers/Shared/SystemGroup/[systemgroup.com.apple.lsd GUID]/Library/Caches/com.apple.lsdidentifiers.plist
/private/var/containers/Shared/SystemGroup/[systemgroup.com.apple.powerlog GUID]/Library/ BatteryLife/CurrentPowerlog.PLSQL
/private/var/mobile/Library/Spotlight/BundleInfo/InstalledApps.plist"
/private/var/mobile/Library/TCC/TCC.db
Once a bundle is found create a new directory somewhere and copy the contents of the bundle into the new directory called “Payload”. Create the archive elsewhere; ensure you do not modify the original image! (You should already be using a copy of the image to maintain evidence integrity, but it can never hurt to double check) Note you may need to omit some files in the directory as they may hinder signing the package.
Copying the contents of the bundle into a Payload directory
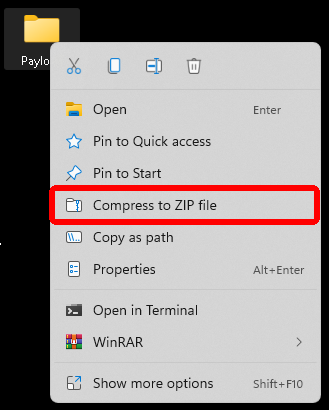
After the contents have been copied, compress the folder to a zip file and rename the zip to “[appname].ipa”. This ipa may now be sideloaded onto another compatible iOS device.
Compressing the Payload directory to a ZIP file
IPA Extraction Via Filza File Manager
The Filza file manager is a file manager application tweak compatible with jailbroken iDevices. Applications which facilitate the jailbreaking process may be installed as IPA files through the methods discussed in the previous chapter. Extracting IPAs through Filza is convenient as the IPA may be exported directly from the device and sent over AirDrop/E-Mail/etc… The following steps will work with other mobile file managers; however, Filza is maintained moreso than other file managers (e.g., the outdated iFile tweak).
Installing Filza
With a jailbroken device head to Cydia, search for “Filza”. Install the Filza file manager. Some devices may not be compatible with the newest version or may require the use of a 32-bit version.
Installing Filza File Manager
Creating an IPA With Filza
With Filza now installed, open the application and head to the application bundle which you wish to backup. The bundle will be contained at “/var/containers/Bundle/Application/[APPGUID]”. Filza intelligently pulls the application name from the GUID and displays this for us.
Click on edit and create a new folder titled “Payload”. Copy the “[appname].app”” directory into the Payload folder. ZIP the payload folder. Rename the ZIP to “[appname].ipa”.
Screenshots of how to create an IPA with Filza
If you wish to preserve the other files in the directory (e.g., iTunesMetadata.plist), simply add them to the archive before zipping.
IPA Extraction Via SSH
The IPA may be created over SSH or another network transfer protocol. This may be useful when a remote connection is visible on a jailbroken device, but device access is not permissible. If SSH is not installed on the device, follow the steps detailed in our “Creating a Full File System Image From a Jailbroken iOS Device” blogpost. The post also details a few more network transfer protocols which may be used to recover application data.
With SSH configured, connect to the device (Using “ssh root@[Device IP]”) and search for the application bundle which you wish to backup. The bundle will be contained within the following directory: “/var/containers/Bundle/Application/[APPGUID]”.
Listing the files related to the applicable bundleID
Once located, exit SSH and use the following command to extract the “.app” folder:
“scp -rp root@[Device IP]:[Full Bundle Path] [Local Output Directory]”
Extracting the application folder via SSH
Another protocol other than scp may be used, use whichever protocol will transfer over the directory. Once the directory is saved to the PC, follow the same steps as outlined with Filza to create the IPA. Create a new “Payload” folder, copy the application bundle into the Payload folder, ZIP the Payload folder, and rename to “[appname].ipa”.