Mobile Forensics Data Structures: Extracting and Analyzing Data with Free Tools
In mobile forensics, uncovering valuable evidence often involves dealing with complex data structures stored within various file formats. Many mobile applications rely on SQLite databases, which can contain vital information, but that data is not always immediately readable. Sometimes, data is embedded in more complex structures like binary property lists (plists). To make things even trickier, you might find a plist embedded within another plist, encoded in Base64.
In this guide, we’ll walk through how to extract and analyze such data structures using entirely free tools: SQLite Browser, Plist Editor Pro, and Notepad++. These tools are widely available and are perfect for forensic investigators who need to work within a budget.
Step 1: Extracting BLOB Data from an SQLite Database Using SQLite Browser
Many mobile applications store data in SQLite databases. SQLite databases commonly store app settings, messages, and cached data, but sometimes they contain binary data, such as images or encoded plists, in BLOB (Binary Large Object) fields. This data can be analyzed with SQLite Browser (a free tool for exploring SQLite files)We have a guide for installing and running SQLite Browser as well as a video tutorial. The following details pick up with the tool already installed.
This can be common throughout a database. It could be in a few entries or make up the entire database. Here, we have an example showing six out of the 43 rows of BLOB data.
Using SQLite Browser, highlight on a BLOB and can see the header denotes this is a binary plist.
Then we want to use SQLite Browser to “Export to file” and save it as a “plist” file.
Note* SQLite does have some nuances in terms of when you should open the database with its correlating WAL file and when you would want to open the database read-only as to not apply the WAL. You can do either with SQLite Browser. We always recommend working on a copy of the database as opening the database with the WAL file will update the database.
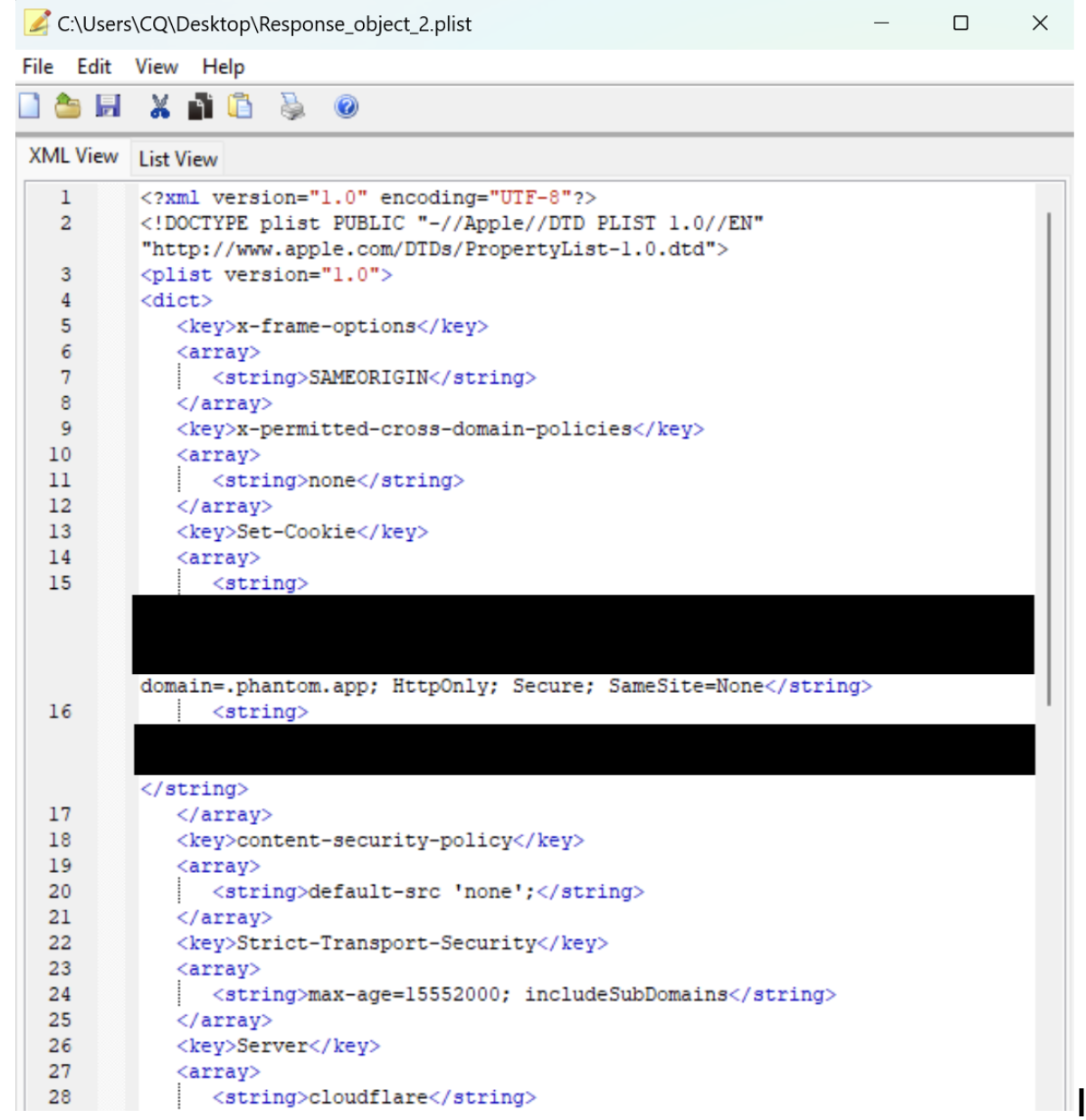
Step 2: Analyzing the BLOB as a Binary Plist Using Plist Editor Pro
From the previous step, we determined the BLOB contains a binary plist (commonly used in iOS apps). We can use Plist Editor Pro (a free plist editor) to open and view this plist. Plist Editor Pro will show the Plist in a more friendly XML view.
When presented with a structured plist, you can explore the contents and look for fields of interest, such as user preferences, app metadata, or other forensic evidence.
In the event that your binary plist data is contained in an NSKey archived, you can use Yogesh Khatri’s tool to make the data viewable. Check out our blog from Sarah Hayes that shares the details on deserializing NSKey archives.
Step 3: Handling Base64-Encoded Data Using Notepad++
Sometimes, a plist may contain additional encoded data, such as a Base64 string, which is often used to encode binary information in a text-friendly format. For example:
This is a Base64-encoded string that needs to be decoded to access the actual data, which may be another plist or file.
Since this looks like Base64, we can copy/paste it into a new file in Notepad++.
Then we can use one of the Plugins to decode the data. We highlight all the data and select Plugins -> MIME Tools -> Base64 Decode.
Once it’s decoded, we can again see that it contains a bplist header.
Now we can do a “Save As” and save this file as a .plist file.
And then we once again open up the newly saved file in plist Editor Pro to reveal another plist.
Conclusion
Mobile forensic investigations often require dealing with complex nested data structures hidden within SQLite databases, binary plists, and Base64-encoded content. We started with a SQLite database, pulled out the BLOB data which was actually a binary plist. One of the records was Base64 encoded and contained another binary plist.
Fortunately, with free tools like SQLite Browser, Plist Editor Pro, and Notepad++, you can fully extract, decode, and analyze such data.
This step-by-step approach will help you navigate through these structures, uncovering the evidence hidden within. Forensic analysis doesn’t always require expensive software—free tools can provide powerful functionality, allowing investigators to work efficiently and effectively.
If you're interested in learning more about mobile forensics, consider taking our comprehensive Hexordia Mobile Forensic Analysis (HMFA) course, which provides an overview of mobile forensics and deep dives into iOS and Android. For those wanting to dive deeper into specific aspects, we also offer a Hexordia Data Structures Course (HDSC) that focuses on analyzing complex data formats.
Our courses are designed to provide hands-on experience and a deeper understanding of forensic techniques, empowering you to become an expert in this growing field. Visit our website to find out more and enroll today!